Sign an Apk With the Upload Certificate
Android requires that all APKs be digitally signed with a certificate earlier they are installed on a device or updated. When releasing using Android App Bundles, you lot need to sign your app bundle with an upload fundamental before uploading it to the Play Panel, and Play App Signing takes care of the residual. For apps distributing using APKs on the Play Store (created before Baronial 2021) or on other stores, you must manually sign your APKs for upload.
This folio guides you through some of import concepts related to app signing and security, how to sign your app for release to Google Play using Android Studio, and how to configure Play App Signing.
The following is a high-level overview of the steps you might need to take to sign and publish a new app to Google Play:
- Generate an upload cardinal and keystore
- Sign your app with your upload central
- Configure Play App Signing
- Upload your app to Google Play
- Prepare & coil out release of your app
If instead your app is already published to the Google Play Shop with an existing app signing key, or y'all would like to choose the app signing primal for a new app instead of having Google generate it, follow these steps:
- Sign your app with your app's signing cardinal and select the option to encrypt and export its signing key.
- Upload your app'southward signing cardinal to Play App Signing.
- (Recommended) Generate and register an upload certificate for future updates to your app
- Upload your app to Google Play
- Set up & roll out release of your app
This page likewise explores how to manage your own keys for when uploading your app to other app stores. If you do not use Android Studio or would rather sign your app from the command line, acquire about how to use apksigner.
Play App Signing
With Play App Signing, Google manages and protects your app's signing key for you lot and uses information technology to sign your APKs for distribution. And, because app bundles defer building and signing APKs to the Google Play Store, yous need to configure Play App Signing before yous upload your app package. Doing then lets you benefit from the following:
- Use the Android App Bundle and support Google Play's advanced delivery modes. The Android App Parcel makes your app much smaller, your releases simpler, and makes it possible to utilize feature modules and offering instant experiences.
- Increase the security of your signing key, and make it possible to employ a separate upload key to sign the app bundle y'all upload to Google Play.
-
One time primal upgrade for new installs lets you modify your app signing key in case your existing one is compromised or if you need to migrate to a cryptographically stronger key
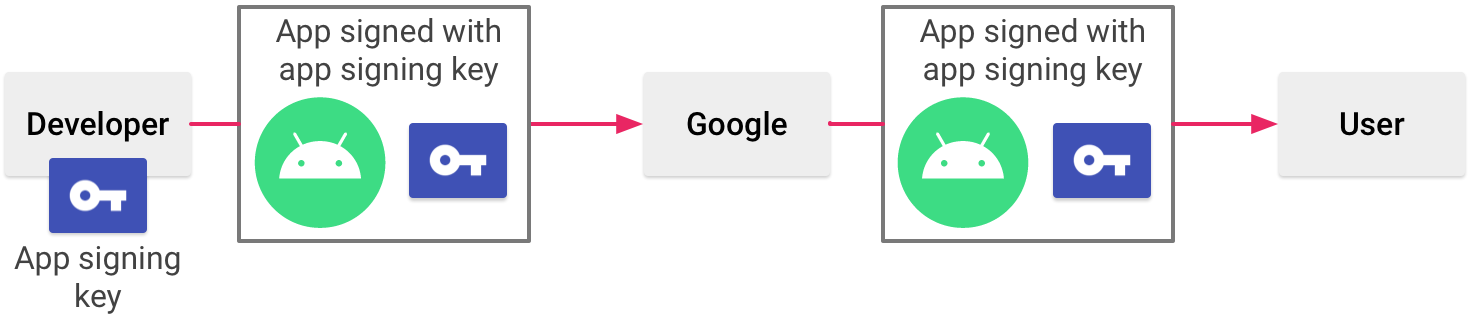
Play App Signing uses 2 keys: the app signing key and the upload key, which are described in further particular in the section about Keys and keystores. You lot proceed the upload fundamental and use it to sign your app for upload to the Google Play Shop. Google uses the upload certificate to verify your identity, and signs your APK(s) with your app signing key for distribution equally shown in figure 1. By using a divide upload fundamental you can request an upload key reset if your key is e'er lost or compromised.
Past comparing, for apps created before August 2021 that accept not opted in to Play App Signing, if you lose your app's signing fundamental, you lot lose the power to update your app.
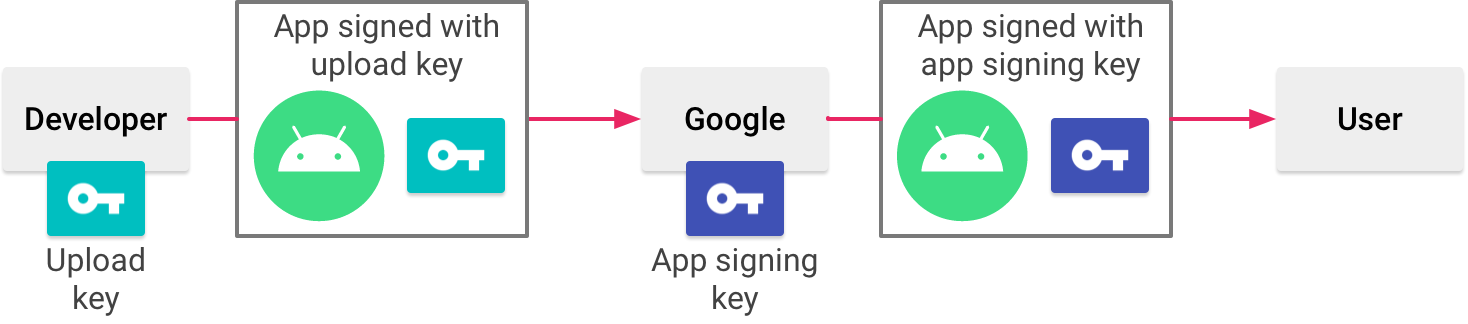
Figure i. Signing an app with Play App Signing
Your keys are stored on the same infrastructure that Google uses to shop its own keys, where they are protected past Google's Cardinal Management Service. You can learn more nigh Google'south technical infrastructure by reading the Google Cloud Security Whitepapers.
When you lot use Play App Signing, if y'all lose your upload key, or if it is compromised, you can contact Google to revoke your old upload key and generate a new one. Because your app signing key is secured past Google, you lot tin continue to upload new versions of your app every bit updates to the original app, even if you modify upload keys. To larn more, read Reset a lost or compromised private upload central.
The next section describes some important terms and concepts related to app signing and security. If you'd rather skip ahead and larn how to set your app for upload to the Google Play Store, go to Sign your app for release.
Keystores, keys, and certificates
Coffee Keystores (.jks or .keystore) are binary files that serve as repositories of certificates and individual keys.
A public key document (.der or .pem files), also known every bit a digital certificate or an identity certificate, contains the public central of a public/private central pair, as well every bit another metadata identifying the owner (for example, name and location) who holds the corresponding private primal.
The following are the different types of keys you should empathize:
- App signing central: The central that is used to sign APKs that are installed on a user'southward device. As part of Android'southward secure update model, the signing key never changes during the lifetime of your app. The app signing key is private and must be kept hole-and-corner. You tin can, all the same, share the document that is generated using your app signing key.
-
Upload central: The central you use to sign the app bundle or APK earlier you upload it for app signing with Google Play. You must keep the upload key secret. All the same, you can share the document that is generated using your upload primal. You may generate an upload key in one of the following ways:
- If you choose for Google to generate the app signing cardinal for you when you opt in, then the key y'all employ to sign your app for release is designated as your upload central.
- If you provide the app signing key to Google when opting in your new or existing app, so you lot have the option to generate a new upload key during or afterwards opting in for increased security.
- If you practice not generate a new upload key, yous proceed to use your app signing key as your upload cardinal to sign each release.
Tip: To keep your keys secure, information technology'south a expert idea to make sure your app signing key and upload key are dissimilar.
Working with API providers
You can download the document for the app signing cardinal and your upload fundamental from the Release > Setup > App Integrity page in the Play Console. This is used to register public key(south) with API providers; information technology's intended to be shared, equally it does non contain your private primal.
A certificate fingerprint is a short and unique representation of a document that is frequently requested past API providers alongside the parcel proper noun to annals an app to use their service. The MD5, SHA-1 and SHA-256 fingerprints of the upload and app signing certificates tin can exist found on the app signing page of the Play Console. Other fingerprints can besides be computed by downloading the original document (.der) from the aforementioned page.
Sign your debug build
When running or debugging your projection from the IDE, Android Studio automatically signs your app with a debug document generated by the Android SDK tools. The first fourth dimension you run or debug your project in Android Studio, the IDE automatically creates the debug keystore and document in $HOME/.android/debug.keystore, and sets the keystore and primal passwords.
Because the debug certificate is created by the build tools and is insecure past design, most app stores (including the Google Play Store) exercise not accept apps signed with a debug certificate for publishing.
Android Studio automatically stores your debug signing information in a signing configuration and then yous practice non accept to enter it every time y'all debug. A signing configuration is an object consisting of all of the necessary data to sign your app, including the keystore location, keystore password, key name, and key password.
For more than data near how to build and run apps for debugging, come across Build and Run Your App.
Expiry of the debug certificate
The cocky-signed certificate used to sign your app for debugging has an expiration date of 30 years from its creation date. When the certificate expires, you get a build fault.
To fix this trouble, only delete the debug.keystore file stored in ane of the following locations:
-
~/.android/on OS X and Linux -
C:\Documents and Settings\user\.android\on Windows XP -
C:\Users\user\.android\on Windows Vista and Windows seven, 8, and ten
The next time you build and run a debug version of your app, Android Studio regenerates a new keystore and debug key.
Sign your app for release to Google Play
When you are ready to publish your app, you need to sign your app and upload it to an app store, such equally Google Play. When publishing your app to Google Play for the first time, you must also configure Play App Signing. Play App Signing is optional for apps created before August 2021. This section shows you how to properly sign your app for release and configure Play App Signing.
Generate an upload cardinal and keystore
If you don't already take an upload primal, which is useful when configuring Play App Signing, you can generate i using Android Studio every bit follows:
- In the menu bar, click Build > Generate Signed Bundle/APK.
- In the Generate Signed Package or APK dialog, select Android App Bundle or APK and click Next.
- Below the field for Fundamental store path, click Create new.
-
On the New Key Store window, provide the following information for your keystore and key, as shown in figure 2.
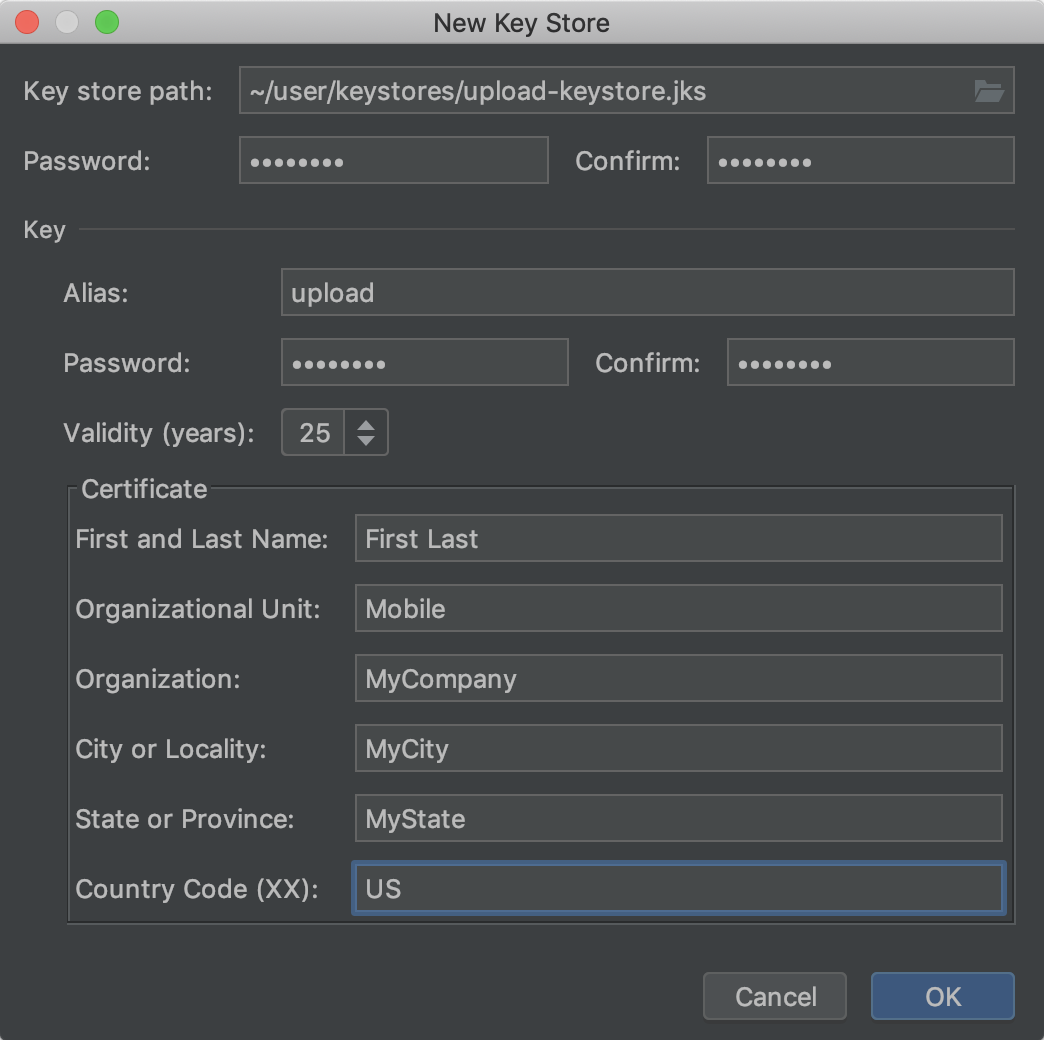
Figure ii. Create a new upload fundamental and keystore in Android Studio.
-
Keystore
- Central store path: Select the location where your keystore should be created. Besides, a file name should exist added to the end of the location path with the
.jksextension. - Password: Create and confirm a secure password for your keystore.
- Central store path: Select the location where your keystore should be created. Besides, a file name should exist added to the end of the location path with the
-
Key
- Allonym: Enter an identifying name for your key.
- Countersign: Create and confirm a secure password for your key. This should be the same as your keystore countersign. (Please refer to the known result for more data)
- Validity (years): Set the length of time in years that your key will be valid. Your fundamental should be valid for at least 25 years, so you can sign app updates with the same key through the lifespan of your app.
- Certificate: Enter some data about yourself for your document. This information is not displayed in your app, but is included in your certificate equally part of the APK.
-
One time y'all complete the form, click OK.
-
If you would like to build and sign your app with your upload key, keep to the section about how to Sign your app with your upload key. If you only want to generate the key and keystore, click Cancel.
Sign your app with your key
If you already have an upload key, use information technology to sign your app. If instead your app is already signed and published to the Google Play store with an existing app signing key, use it to sign your app and make certain to encrypt and consign information technology to opt your app in to Play App Signing. Yous can afterward generate a separate upload key and register your upload fundamental's public certificate with Google Play to sign and upload subsequent updates to your app.
To sign your app using Android Studio, and export an existing app signing fundamental, follow these steps:
- If you lot don't currently accept the Generate Signed Bundle or APK dialog open, click Build > Generate Signed Bundle/APK.
- In the Generate Signed Parcel or APK dialog, select either Android App Bundle or APK and click Next.
- Select a module from the drop down.
-
Specify the path to your keystore, the alias for your key, and enter the passwords for both. If you oasis't yet prepared your upload keystore and central, beginning Generate an upload key and keystore and then render to consummate this stride.
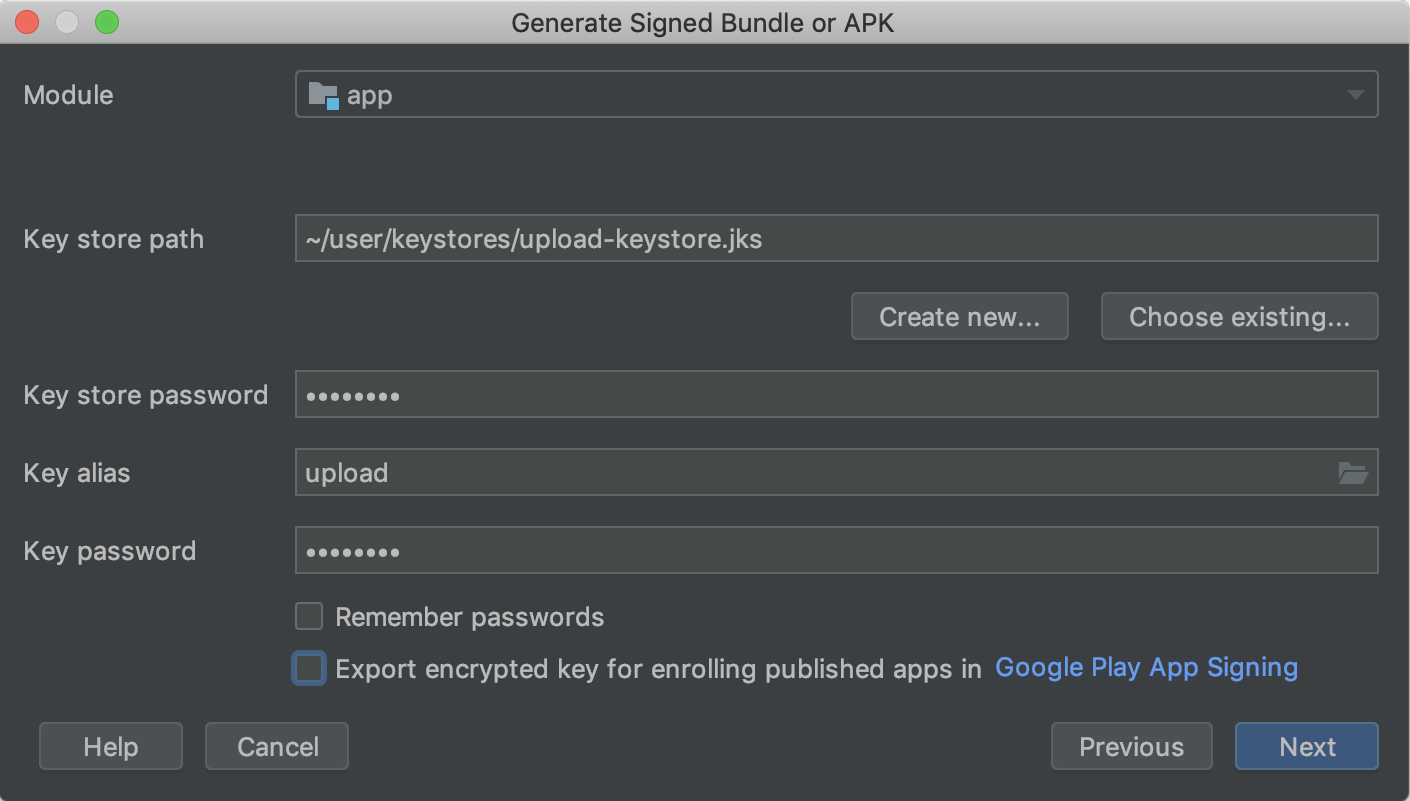
Figure iii. Sign your app with your upload key.
-
If you're signing an app package with an existing app signing primal, and you'd similar to afterward opt your app in to Play App Signing, bank check the box next to Export encrypted key and specify a path to relieve your signing cardinal equally an encrypted
*.pepkfile. Yous can then use your encrypted app signing key to opt in an existing app into Play App Signing. -
Click Next.
-
In the next window (shown in effigy 4), select a destination binder for your signed app, select the build blazon, choose the product season(southward) if applicable.
-
If yous are building and signing an APK, you need to select which Signature Versions you want your app to back up. To learn more than, read virtually app signing schemes
-
Click Finish.
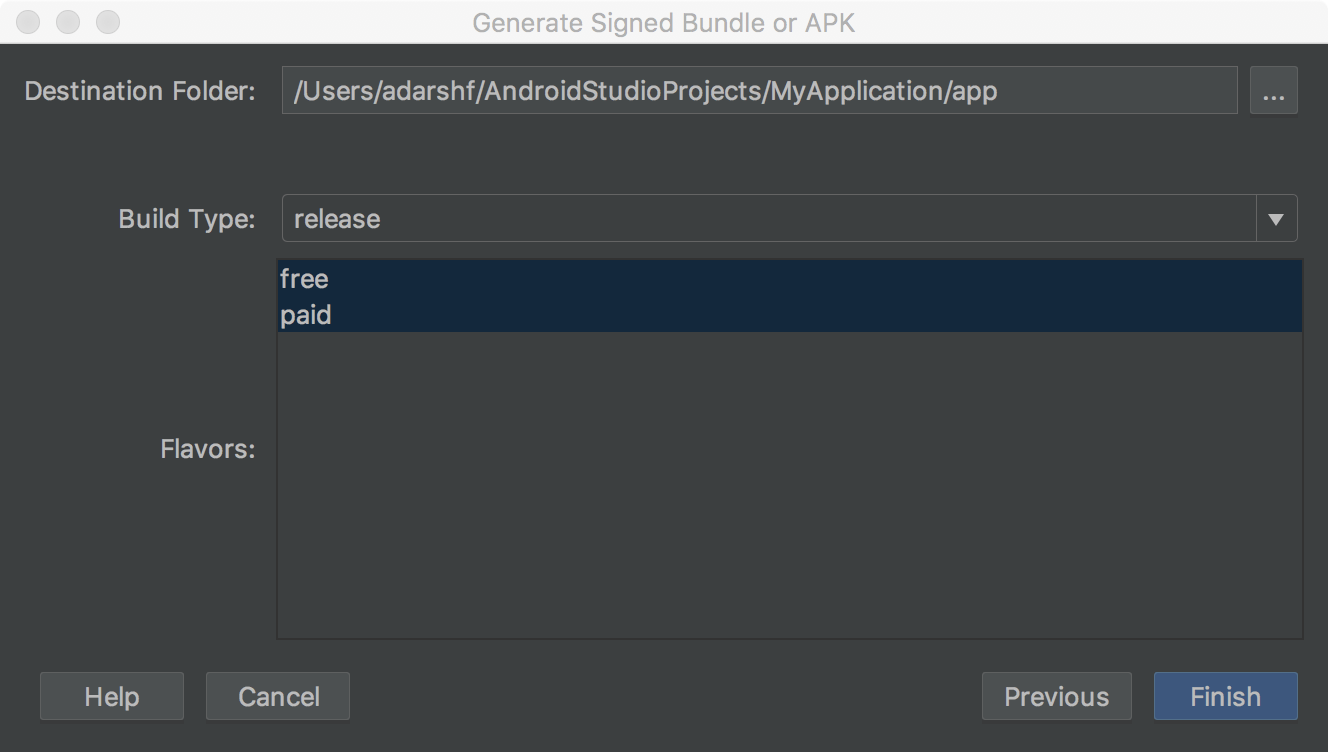
Figure four. Generate a signed version of your app for the selected product flavors.

Figure 5. Click the link in the popup to analyze or locate your app package, or locate your exported signing primal.
After Android Studio finishes building your signed app, y'all tin can either locate or analyze your app past clicking on the appropriate choice in the pop-up notification. If you selected the option to export your signing cardinal, you tin can quickly navigate to it by clicking the dropdown pointer in the bottom right corner of the popup to aggrandize it and clicking Show Exported Fundamental File, every bit shown in figure 5.
Now you're gear up to opt your app in to Play App Signing and upload your app for release. If you're new to the app publishing process, you may want to read the Launch overview. Otherwise, go on to the page well-nigh how to Upload your app to the Play Console.
Using Play App Signing
Every bit described before in this page, configuring Play App Signing is required to sign your app for distribution through Google Play (except for apps created before August 2021, which may continue distributing self-signed APKs). The steps y'all need to have depend on whether your app has not yet been published to Google Play, or your app is already signed and was published before Baronial 2021 using an existing app signing key.
Configure a new app
To configure signing for an app that has not all the same been published to Google Play, go along as follows:
- If y'all haven't already washed then, generate an upload key and sign your app with that upload key.
- Sign in to your Play Console.
- Follow the steps to set & ringlet out your release to create a new release.
- After you cull a release rails, configure app signing under the App Integrity section as follows:
- To have Google Play generate an app signing key for yous and employ it to sign your app, yous don't take to exercise anything. The key yous utilize to sign your outset release becomes your upload fundamental, and you should use it to sign futurity releases.
- To use the aforementioned key as another app on your developer account, select Change app signing cardinal > Use my own key > Use the same key as another app in this account, select an app, and then click Continue.
- To provide your own signing key for Google to use when signing your app, select Alter app signing primal > Apply my ain key and select one of the options that lets y'all securely upload a individual key and its public certificate.
In the section chosen App Bundles, click Browse files to locate and upload the app you signed using your upload fundamental. For more information well-nigh releasing your app, refer to prepare & gyre out your release. When yous release your app after configuring Play App Signing, Google Play generates (unless you upload an existing key) and manages your app'south signing key for you. Simply sign subsequent updates to your app using your app's upload key before uploading it to Google Play.
If y'all need to create a new upload key for you app, go to the section well-nigh how to Reset a lost or compromised private upload key.
Opt in an existing app
If you're updating an app that's already published to Google Play using an existing app signing cardinal, you can opt in to Play App Signing as follows:
- If y'all haven't already done so, sign your app using Android Studio with your existing app signing cardinal and make sure to cheque the box next to Export encrypted key to save your signing key as an encrypted
*.pepkfile. You'll demand this file in a later step. This can also be washed using the PEPK tool, which you tin download from the Play Console. - Sign in to your Play Panel and navigate to your app.
- On the left carte, click Release > Setup > App integrity.
- If applicable, review the Terms of Service and select Accept.
- Select one of the options that best describes the signing central you want to upload to Google Play and follow the instructions that are shown. For example, if you used Android Studio to export your app's signing cardinal, as described on this page, select Upload a primal exported from Android Studio and upload the
*.pepkfile for your key. - Click Enroll.
Y'all should at present see a page with the details of your app'south signing and upload certificates. Google Play now signs your app with your existing key when deploying information technology to users. However, one of the most important benefits to Play App Signing is the ability to separate the central you use to sign the artifact yous upload to Google Play from the central that Google Play uses to sign your app for distribution to users. So, consider following the steps in the next section to generate and register a dissever upload central.
Generate and register an upload certificate
When you're publishing an app that is not signed past an upload key, the Google Play Console provides the option to register one for futurity updates to the app. Although this is an optional stride, it's recommended that y'all publish your app with a primal that'due south split up from the one Google Play uses to distribute your app to users. That way, Google keeps your signing key secure, and you have the option to reset a lost or compromised private upload cardinal. This section describes how to create an upload key, generate an upload certificate from it, and register that certificate with Google Play for future updates of your app.
The post-obit describes the situations in which you see the choice to register an upload document in the Play Console:
- When you publish a new app that's signed with a signing primal and opt it in to Play App Signing.
- When you are most to publish an existing app that'due south already opted in to Play App Signing, but information technology is signed using its signing central.
If you are not publishing an update to an existing app that's already opted in to Play App Signing, and you lot'd like to register an upload certificate, complete the steps below and continue on to the department about how to reset a lost or compromised individual upload fundamental.
If you oasis't already done so, generate an upload cardinal and keystore.
After you create your upload key and keystore, you lot need to generate a public certificate from your upload cardinal using keytool, with the post-obit control:
$ keytool -consign -rfc -keystore your-upload-keystore.jks -alias upload-alias -file output_upload_certificate.pem
Now that you have your upload document, register it with Google when prompted in the Play Console or read the section below to register it though the Google Play support squad.
Upgrade your app signing cardinal
In some circumstances, you might want to modify your app's signing central. For example, because you desire a cryptographically stronger key or your signing key has been compromised. However, considering users tin can only update your app if the update is signed with the same signing key, it's difficult to alter the signing key for an app that's already published.
If you publish your app to Google Play, you can upgrade the signing fundamental for your published app through the Play Panel—your new cardinal is used to sign new installs and app updates, while your older app signing key is used to sign updates for users who installed your app before the key upgrade.
To learn more than, read Upgrade your app signing central for new installs.
Reset a lost or compromised private upload key
If y'all lost your individual upload key or your private key has been compromised, y'all can create a new one and contact the Google Play back up team to reset the primal.
Configure the build process to automatically sign your app
In Android Studio, you can configure your project to sign the release version of your app automatically during the build procedure by creating a signing configuration and assigning it to your release build type. A signing configuration consists of a keystore location, keystore password, key alias, and cardinal countersign. To create a signing configuration and assign information technology to your release build type using Android Studio, consummate the post-obit steps:
- In the Project window, right click on your app and click Open Module Settings.
- On the Projection Structure window, nether Modules in the left console, click the module you would like to sign.
- Click the Signing tab, then click Add together
 .
. -
Select your keystore file, enter a proper name for this signing configuration (equally you lot may create more 1), and enter the required information.
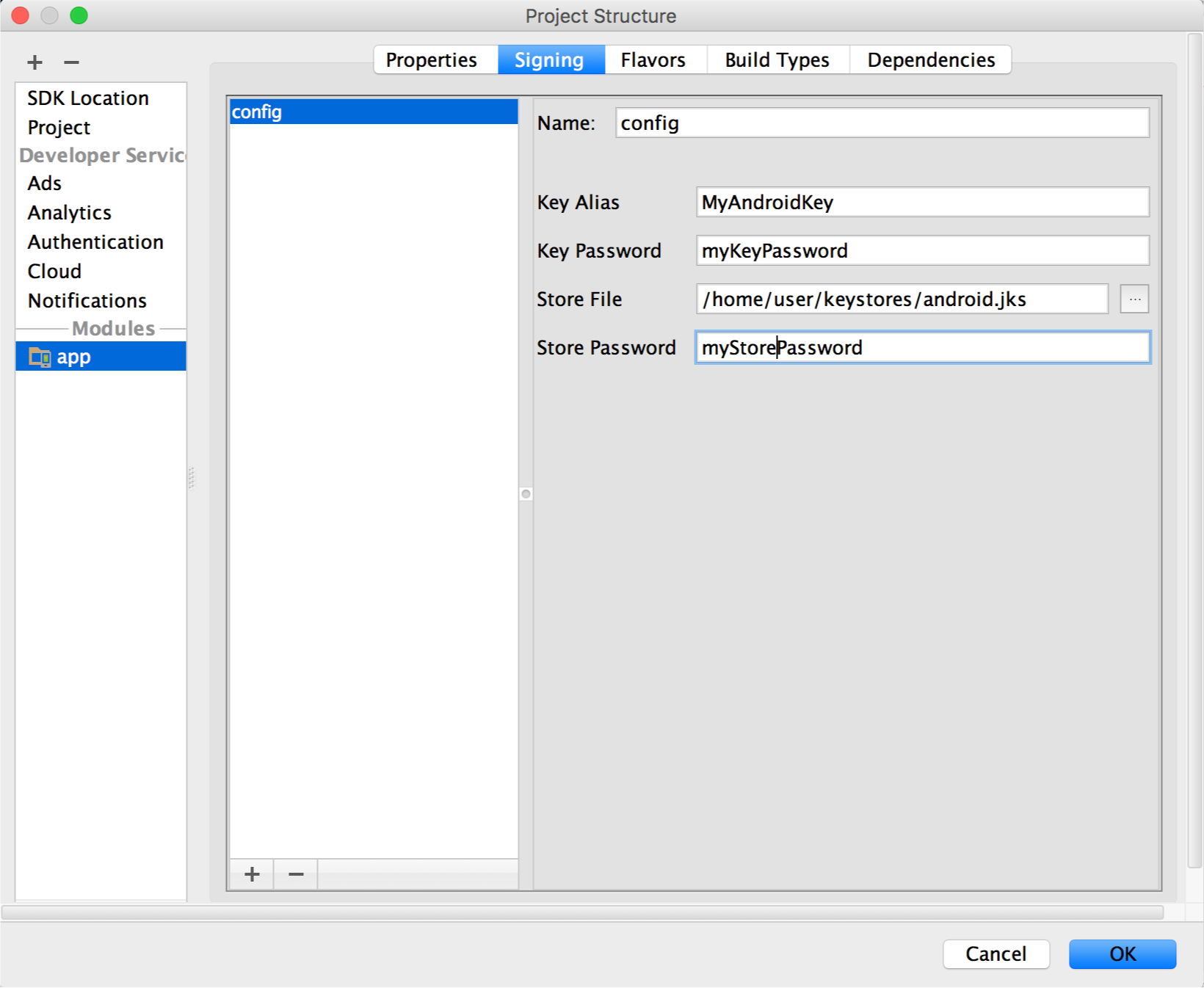
Figure 7. The window for creating a new signing configuration.
- Click the Build Types tab.
- Click the release build.
-
Under Signing Config, select the signing configuration yous just created.
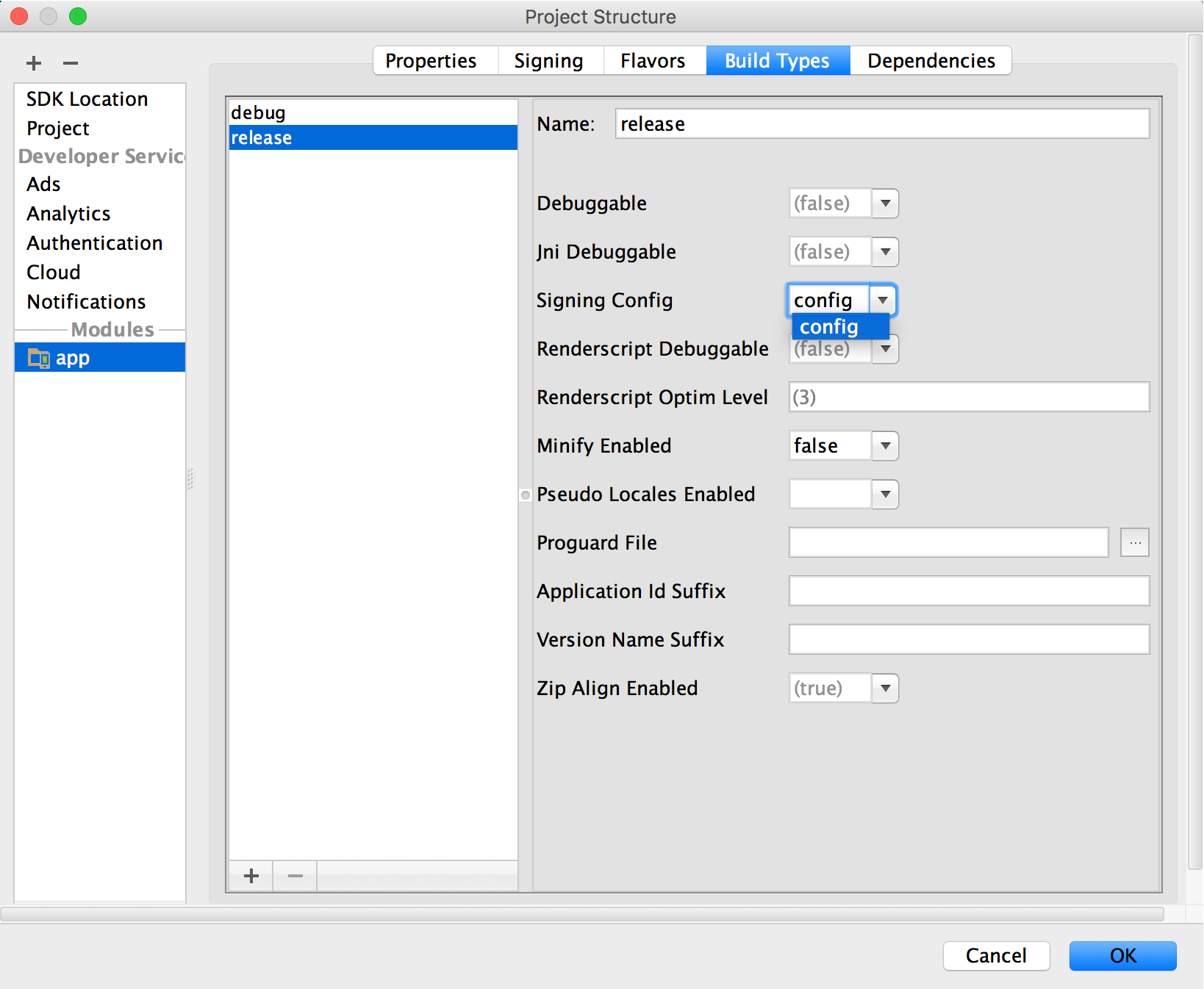
Figure 8. Select a signing configuration in Android Studio.
- Click OK.
Now every time you build your release build type past selecting an choice under Build > Build Packet(south) / APK(s) in Android Studio, the IDE will sign your app automatically, using the signing configuration you specified. You can discover your signed APK or app bundle in the build/outputs/ directory inside the project directory for the module you are building.
When y'all create a signing configuration, your signing data is included in obviously text in your Gradle build files. If y'all are working in a team or sharing your code publicly, you lot should keep your signing information secure by removing it from the build files and storing it separately. Y'all tin read more nearly how to remove your signing data from your build files in Remove Signing Information from Your Build Files. For more than well-nigh keeping your signing information secure, read Secure your key.
Sign each product season differently
If your app uses product flavors and y'all would like to sign each season differently, you tin can create additional signing configurations and assign them past flavor:
- In the Project window, right click on your app and click Open Module Settings.
- On the Project Structure window, under Modules in the left panel, click the module you lot would like to sign.
- Click the Signing tab, then click Add
 .
. -
Select your keystore file, enter a name for this signing configuration (as you may create more than one), and enter the required information.

Figure 10. The window for creating a new signing configuration.
- Echo steps 3 and four every bit necessary until you have created all your signing configurations.
- Click the Flavors tab.
- Click the flavour yous would like to configure, then select the advisable signing configuration from the Signing Config dropdown menu.
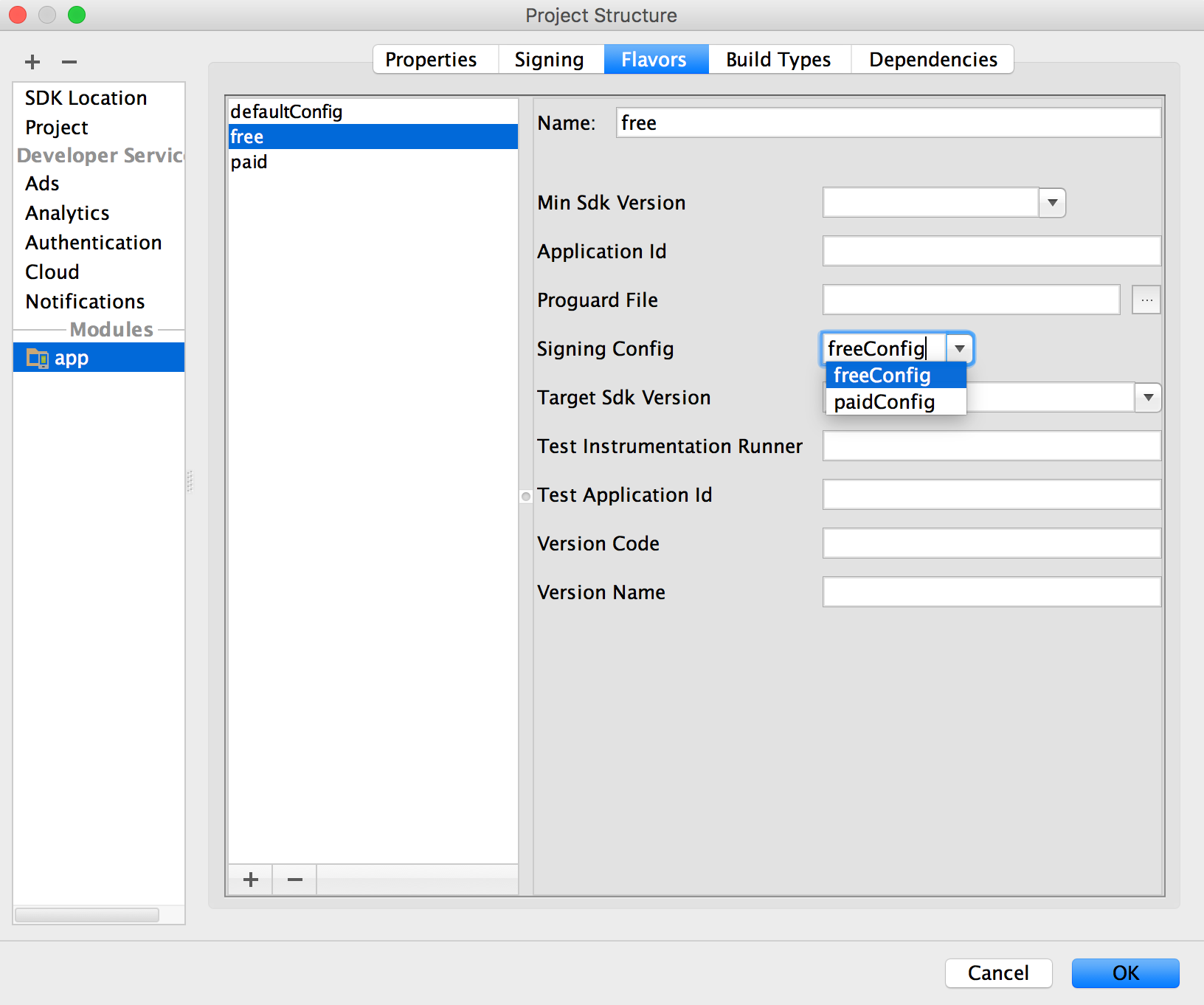
Figure 11. Configure signing settings by production flavor.
Repeat to configure any additional product flavors.
- Click OK.
Yous tin also specify your signing settings in Gradle configuration files. For more information, come across Configuring Signing Settings.
Manage your own signing fundamental
If yous cull not to opt in to Play App Signing (only for apps created before August 2021), you tin manage your own app signing key and keystore. Go along in listen, yous are responsible for securing the fundamental and the keystore. Additionally, your app will not be able to support Android App Bundles, Play Feature Delivery and Play Asset Commitment.
When you are ready to create your own key and keystore, make sure you starting time choose a stiff password for your keystore and a separate strong password for each private key stored in the keystore. Y'all must keep your keystore in a safe and secure place. If yous lose access to your app signing key or your cardinal is compromised, Google cannot retrieve the app signing fundamental for you, and you will not be able to release new versions of your app to users as updates to the original app. For more information, see Secure your key, below.
If you manage your own app signing primal and keystore, when you sign your APK, you will sign it locally using your app signing key and upload the signed APK directly to the Google Play Store for distribution as shown in effigy ten.
Effigy 12. Signing an app when yous manage your own app signing key
When y'all utilize Play App Signing, Google keeps your signing cardinal safe, and ensures your apps are correctly signed and able to receive updates throughout their lifespans. However, if yous decide to manage your app signing central yourself, at that place are a few considerations you lot should keep in mind.
Signing considerations
You should sign your app with the aforementioned document throughout its expected lifespan. There are several reasons why you should do so:
- App upgrade: When the system is installing an update to an app, information technology compares the certificate(s) in the new version with those in the existing version. The system allows the update if the certificates match. If you sign the new version with a dissimilar certificate, you must assign a different bundle proper noun to the app—in this case, the user installs the new version every bit a completely new app.
- App modularity: Android allows APKs signed by the same certificate to run in the same procedure, if the apps so request, so that the system treats them equally a single app. In this mode y'all can deploy your app in modules, and users can update each of the modules independently.
- Code/data sharing through permissions: Android provides signature-based permissions enforcement, and so that an app can expose functionality to another app that is signed with a specified certificate. Past signing multiple APKs with the same document and using signature-based permissions checks, your apps tin share lawmaking and information in a secure way.
If you plan to support upgrades for an app, ensure that your app signing key has a validity catamenia that exceeds the expected lifespan of that app. A validity flow of 25 years or more is recommended. When your key's validity period expires, users will no longer be able to seamlessly upgrade to new versions of your app.
If y'all plan to publish your apps on Google Play, the cardinal you apply to sign your app must take a validity menstruum catastrophe later 22 Oct 2033. Google Play enforces this requirement to ensure that users tin can seamlessly upgrade apps when new versions are available.
Keep your key secure
If you lot choose to manage and secure your app signing primal and keystore yourself (instead of opting in to Play App Signing), securing your app signing key is of critical importance, both to y'all and to the user. If yous allow someone to use your key, or if you lot leave your keystore and passwords in an unsecured location such that a 3rd-party could find and apply them, your authoring identity and the trust of the user are compromised.
If a third party should manage to take your app signing cardinal without your knowledge or permission, that person could sign and distribute apps that maliciously replace your authentic apps or decadent them. Such a person could also sign and distribute apps under your identity that attack other apps or the system itself, or decadent or steal user data.
Your private cardinal is required for signing all future versions of your app. If you lose or misplace your key, you will not exist able to publish updates to your existing app. You cannot regenerate a previously generated central.
Your reputation equally a developer entity depends on your securing your app signing key properly, at all times, until the key is expired. Here are some tips for keeping your cardinal secure:
- Select strong passwords for the keystore and key.
- Do non requite or lend anyone your private central, and exercise not let unauthorized persons know your keystore and key passwords.
- Keep the keystore file containing your private fundamental in a safety, secure place.
In general, if y'all follow common-sense precautions when generating, using, and storing your key, it will remain secure.
Remove signing data from your build files
When yous create a signing configuration, Android Studio adds your signing information in patently text to the module's build.gradle files. If you lot are working with a team or open-sourcing your lawmaking, y'all should movement this sensitive data out of the build files and so it is not easily accessible to others. To practice this, you should create a separate properties file to store secure information and refer to that file in your build files equally follows:
- Create a signing configuration, and assign it to one or more build types. These instructions presume you lot have configured a single signing configuration for your release build type, as described in Configure the build process to automatically sign your app, above.
- Create a file named
keystore.backdropin the root directory of your project. This file should contain your signing data, as follows:storePassword=myStorePassword keyPassword=mykeyPassword keyAlias=myKeyAlias storeFile=myStoreFileLocation
- In your module'due south
build.gradlefile, add code to load yourkeystore.propertiesfile before theandroid {}block.Groovy
... // Create a variable called keystorePropertiesFile, and initialize it to your // keystore.backdrop file, in the rootProject folder. def keystorePropertiesFile = rootProject.file("keystore.properties") // Initialize a new Properties() object called keystoreProperties. def keystoreProperties = new Properties() // Load your keystore.backdrop file into the keystoreProperties object. keystoreProperties.load(new FileInputStream(keystorePropertiesFile)) android { ... }Kotlin
... import java.util.Properties import coffee.io.FileInputStream // Create a variable called keystorePropertiesFile, and initialize information technology to your // keystore.properties file, in the rootProject binder. val keystorePropertiesFile = rootProject.file("keystore.properties") // Initialize a new Properties() object chosen keystoreProperties. val keystoreProperties = Backdrop() // Load your keystore.properties file into the keystoreProperties object. keystoreProperties.load(FileInputStream(keystorePropertiesFile)) android { ... }Note: You could choose to store your
keystore.propertiesfile in some other location (for example, in the module folder rather than the root binder for the project, or on your build server if you are using a continuous integration tool). In that case, yous should change the lawmaking higher up to correctly initializekeystorePropertiesFileusing your actualkeystore.propertiesfile's location. - Y'all can refer to properties stored in
keystorePropertiesusing the syntaxkeystoreProperties['propertyName']. Alter thesigningConfigsblock of your module'sbuild.gradlefile to reference the signing information stored inkeystorePropertiesusing this syntax.Groovy
android { signingConfigs { config { keyAlias keystoreProperties['keyAlias'] keyPassword keystoreProperties['keyPassword'] storeFile file(keystoreProperties['storeFile']) storePassword keystoreProperties['storePassword'] } } ... }Kotlin
android { signingConfigs { getByName("config") { keyAlias = keystoreProperties["keyAlias"] keyPassword = keystoreProperties["keyPassword"] storeFile = file(keystoreProperties["storeFile"]) storePassword = keystoreProperties["storePassword"] } } ... } - Open the Build Variants tool window and ensure that the release build blazon is selected.
- Select an pick under Build > Build Bundle(southward) / APK(s) to build either an APK or app bundle of your release build. Y'all should see the build output in the
build/outputs/directory for your module.
Because your build files no longer incorporate sensitive data, you tin can now include them in source control or upload them to a shared codebase. Be certain to keep the keystore.properties file secure. This may include removing it from your source command organisation.
douglassfrone1952.blogspot.com
Source: https://developer.android.com/studio/publish/app-signing
0 Response to "Sign an Apk With the Upload Certificate"
Post a Comment